Difference between revisions of "Network"
| Line 27: | Line 27: | ||
Suggestions / comments? | Suggestions / comments? | ||
| + | |||
| + | |||
| + | == Server 1 == | ||
| + | |||
| + | Fanless Via Epia Mini-ITX 533MHz | ||
| + | |||
| + | * Low power so fine for always-on. | ||
| + | * Has parallel port! | ||
| + | * Has serial port! | ||
| + | * Ripe for [[HackSpace Instrumentation]] | ||
| + | |||
| + | [[User:Msemtd|Michael Erskine]] 13:11, 10 February 2011 (GMT) | ||
Revision as of 13:11, 10 February 2011
Network
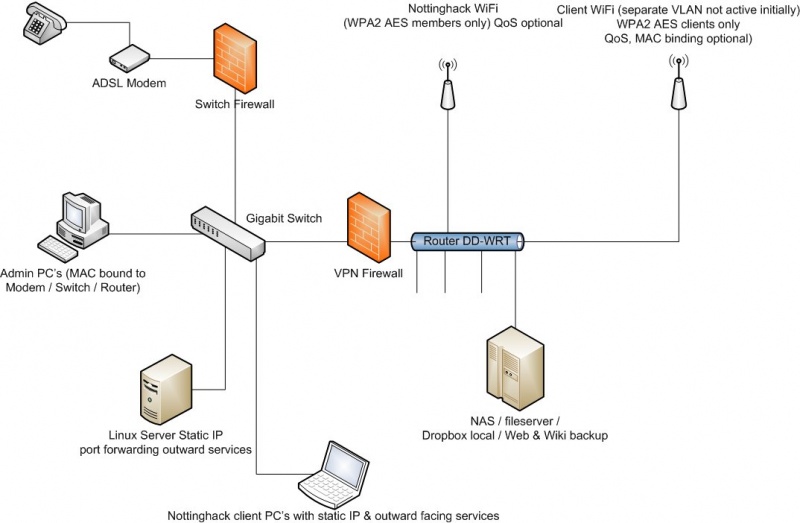
This page will be used for discussion of the proposed network topology & for suggestions for network design / modification.
IP address ranges can be decided on implementation & set to sensible ranges, with reserved IP's outside of DHCP, unless there are any specific requirements.
The above config sets anything connected directly to the switch as a 1st level DMZ, aimed for services / clients that need to be outwardly facing with little / no restrictions.
All machines / services connected via the router are designed to allow access to the internet, and to services or resources, but not remote access from the internet (unless via the VPN - not enabled initially).
The router would offer 2 WiFi access points - 1 for Nottinghack permanent members & 1 for potential clients (Anthem films etc).
These would be on seperate VLANS - the Nottinghack VLAN would have access to local resources - e.g. a future NAS file-share, a local dropbox server for projects & collaborations, a backup of all Web / Wiki files (to allow a remote restore in the event of moving hosts / outage of services) and anything else we don't want to be web facing.
The VPN (when enabled) would allow remote management of the VLANS, which could come in handy in the event of issues with the client WiFi access point.
- Note: the Admin PC would not be a static machine, rather the switch would be configured to only allow admin access to designated machines, via MAC binding, as well as knowledge of the required login's etc. This would help prevent any user with physical access to the switch to alter the permissions / settings unless they were an "Authorised user". As far as "Authorised users" go, I'd suggest that anyone who is a permanent member, with access to all of the key-codes & building key should be eligible. Usual rules apply, as to any tool - if you don't know how to use it / don't do anything :)
I'm undecided about remote management of the gigabit switch, as I've yet to check out it's functionality / certificate management.
Suggestions / comments?
Server 1
Fanless Via Epia Mini-ITX 533MHz
- Low power so fine for always-on.
- Has parallel port!
- Has serial port!
- Ripe for HackSpace Instrumentation
Michael Erskine 13:11, 10 February 2011 (GMT)